Monitoring and Securing
Your Networks
The Hacker Blocker Cybersecurity Operations Center
Stay Ahead of Emerging Threats
Our incident response team detects and responds within minutes of a single cyber-attack, protecting all subscribers.
Detection
Each of our clients have 3rd party detection systems that report attacks to our CSOC every hour of every day.
Response
Attackers are reported & blocked from the subscriber's server automatically while we trace the IP, find the CIDR and cross-reference with Abuse Databases.
The More They Attack Us, The Stronger We Become.
Update & Test
Verified IPs are consolidated into CIDRs and added to the Master Blocklist, if they meet strict criteria to ensure legitimate traffic is unaffected.
Automated Firewall Updates
Within minutes, every subscriber downloads the new Rulesets to their firewalls, pro-actively protecting all subscribers when only one is attacked.
Below is a Live Map of cyberattacks in real-time.
Our subscribers are blocking over 90% of these attacks.
Attack Detection
We use SIEMs and other tools to trace ongoing attacks to their source while the attack is in progress.
Abuse Research
Our tools cross-match the IP to multiple abuse reporting databases, then obtains the CIDR if it meets our criteria.
Real-Time Processing
Within minutes, the IP and / or CIDR is added to the Master Blocklist, which is downloaded every hour by all subscribers.
The Master Blocklist
Our Master Blocklist is the culmination of years of work from thousands of sources around the world. Combining databases from abuse reporting websites, Government sources and cyber-attacks on our own clients, we've created one of the most comprehensive lists of IP addresses and CIDRs used by C2 Commanders, Bot-Nets, Spammers, Hackers and Malware / Ransomware servers.
Most blocked IPs are compromised devices and web hosting servers, not people. We take great care in our IP blocks, and provide unblock request pages for all websites that have Hacker Blocker Hosting.

24/7 Detection and Blocking
Each of our clients have detection and reporting software for common attacks such as SQL Injections, WP-Admin Logins, DDoS attacks, Session attacks and much more. After 3 attacks, the IP is blocked on the local server.
People Behind The Keyboard
Every attack is reported to our staff in real-time, allowing them to research them for abuse and traced to the source. If the IP or CIDR meets the criteria, it is added to the Master Blocklist immediately.
Automated Distribution
Hacker Blocker downloads the Master Blocklist to the native Windows firewall Rules or updates Linux CSF via sFTP every hour. When one client is attacked, all clients are protected within minutes.
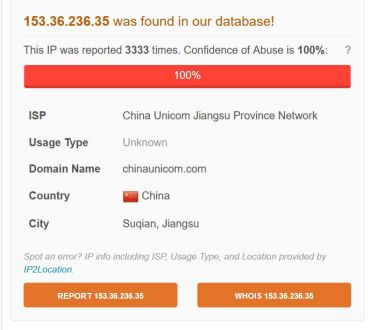
Abuse Database Sources
Sites like AbuseIPDB.com allow people to report cyber-attacks in detail, including type of attack and IP address. This is one of the many tools we use for research, and to find the most egregious attackers before they attack us.
Patterns in the Chaos
With only 4.6 billion IP addresses in the world, hackers don't have unlimited resources to use, although it may seem hopeless during a DDoS attack. We're blocking 90% of their hacker networks, representing 20% of the Internet.
Government Partnerships
By working with government agencies, Hacker Blocker keeps up with the latest alerts and reported IP addresses of cyber threats before they attack our clients. RaaS & malware servers are researched and added routinely.
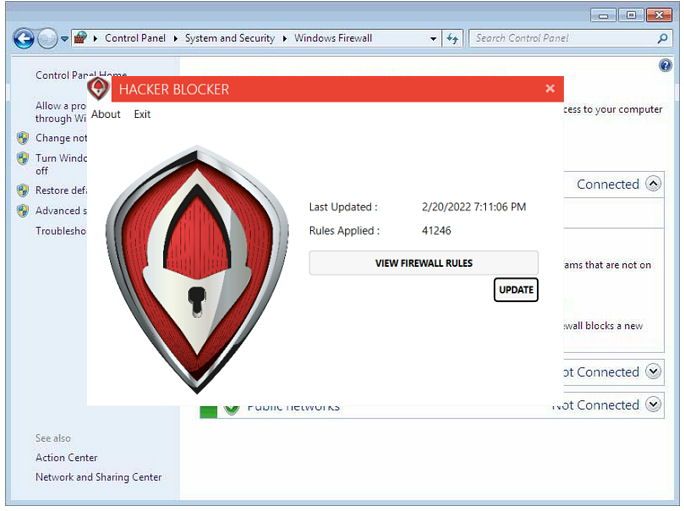
Firewall Updates
The core of the Hacker Blocker solution is the automated distribution of the Master Blocklist.
Windows - Hacker Blocker for Windows Server or PC updates the native Windows Firewall Rules every hour.Treated as a Single Network
Each subscriber is part of our detection network, each contributing to our crowdsourced blocklist.

