The Only Crowdsourced Firewall
Updating Software & Service
Blocking over 770,000,000 Malicious IPs
Hacker Blocker is a software and service that updates the Native Windows Firewall with years of attack data, detects & reports new attacks, and receives hourly updates.
The More They Attack Us, The Stronger We Become

Hacker Blocker is a powerful cybersecurity tool that can help protect your devices and networks from cyber threats, and increase performance.
Upon Installation, Hacker Blocker downloads the latest Master Blocklist and applies years of reported IP addresses to your endpoints instantly.
Our CSOC monitors and stops new threats in real-time, not just for the attacked computer & network, but for every subscriber within minutes.
Easy
Deployment
Installs in seconds on any Windows version, automatically updates the Windows Firewall Rules.
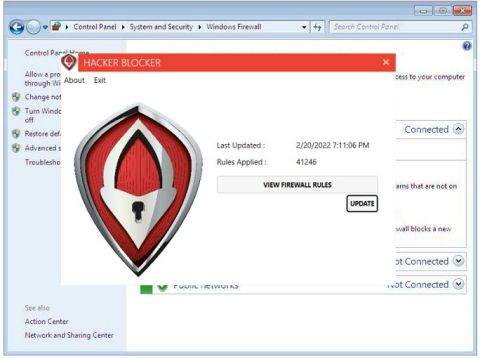
Windows Server and PC
Download and install either the Server or PC version to deploy the Hacker Blocker firewall updater program. It will download and apply the latest Rules for your Windows firewall.
Linux / LAMP
For Dedicated Linux / Apache Servers, we upload a new .deny file via sFTP to your csf firewall every 15 minutes, keeping it secure proactively.
Web Hosting Services
We can transfer your website to our VPS hosting servers quickly, then edit your DNS to point to our servers. Standard websites can be transferred within a single day.

Continuous Updates
24/7/365
Hacker Blocker for Windows Server, 10 or 11 connects to our servers 24 times per day to check for updated Rules to apply. Our Blocklist changes multiple times per day as IPs and CIDRs are added, consolidated or removed.
Linux subscribers receive updated csf.deny files from our servers via sFTP upload every 15 minutes.
Our VPS Hosting clients are behind our main firewall, giving them instant protection from reported attacks.
Each firewall Rule is vetted and verified before inclusion in the Blocklist, to ensure legitimate traffic is not affected.
VPS Web
Hosting
Hacker Blocker Hosting is the only Fully Managed Hosting that blocks millions of known hackers, spammers and bots, detects attacks, and automatically blocks them from all of our clients in real-time.
Our ultra-fast hosting servers have 99.996% uptime, include unlimited bandwidth, email accounts and plenty of space to accommodate any sized website.

Dedicated Linux
Servers / LAMP
Our automated system update your Linux csf files every 15 minutes via sFTP with fresh IP addresses and CIDRs of verified hackers, spammers and bad bots.
We also block Ransomware-as-a-Service (RaaS) servers and other IPs reported by the CISA and other Government Agencies, keeping your websites free of phishers, hackers, spam and Botnets.

Secure & Synchronize
All Endpoints
Protect your websites, email, workstations, laptops, office servers and Virtual Machines with a single solution. If one endpoint is attacked, all are protected from that attacker in minutes.
We use the SOLO Licensing system to help you track installation keys, for complete network coverage and management.

Hacker Blocker for
Windows Server and PC
Hacker Blocker works by updating the native firewall of Windows with thousands of consolidated Rules to block millions of verified hackers, spammers, phishing servers and botnets from your server, PC or laptop.
Each of these entries are researched & verified in real-time, as attack reports are received by our specialists. Once verified, they are added to our Master Blocklist, which is downloaded and applied to your Firewall automatically every hour.
When one client is attacked, all become protected from that attacker - within minutes.
Server Performance Boost,
More Available Bandwidth
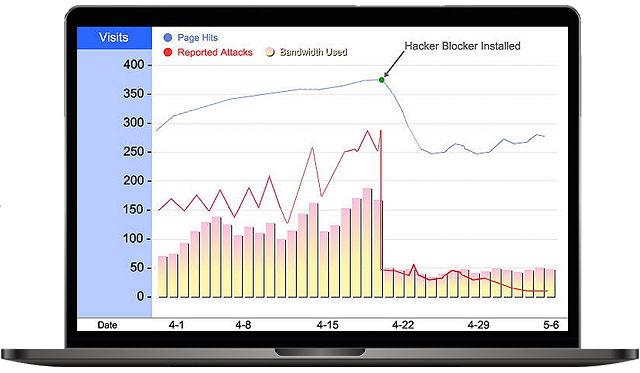
Instant Results
Public-facing servers suffer a barrage of attacks every minute of every day. Hacker Blocker stops many of these attacks instantly.
- Faster Servers & Network
- More Available Bandwidth
- Drastic Reduction in Attacks
- Increased Traffic to Websites
Web servers have reported up to a 300% increase in speed, with significant drops in pageload time.
Hourly Firewall Updates
Your Server and workstation Firewalls are constantly updated, blocking millions of IPs used by:
- Hackers
- Form and Mail Spammers
- Botnets & Zombie Armies*
- Ransomware-as-a-Service Servers
*Zombie Armies are networks of hijacked computers like web servers, aka Malware Botnets. 30,000 websites are compromised each day worldwide and added to these robot-networks.
Simple, flexible pricing.
Choose either Windows Server or PC versions and buy online now. Custom volume licensing is available, contact us to speak to a license specialist.
Windows PC
$30
Per PC / per month
-
Single User License
-
Works on Windows 10, 11PCs and Laptops
-
Single ActivationMultiple Device Licensing Options
-
24/7 Firewall Updates
-
Phone and Email Support
Windows Server
$8
Per user / per month
-
Min 25 User - $199 per month
-
Volume Licensing OptionsFor Enterprise & Datacenter Editions
-
Multiple ActivationsTransferable License
-
24/7 Firewall Updates
-
Phone and Email Support
Frequently Asked
Questions
Hacker Blocker for Windows Licensing
Windows PC - Single user license is for one Activation on a single device. You can move an Activation from one device to another 3 times, called 'Deactivations' per license. If you need more Deactivations, you can request them in your Customer License Portal or call support.
Windows Server edition - Licenses are assigned to a physical OSE of Windows Server for up to 25 users or virtual OSEs, with two activations assigned. For Enterprise and Datacenter editions with more than 25 OSEs, contact our Volume License department.
Volume Licenses can be ordered online or by calling our sales department at (617) 819-5877. We can also customize your license options for easy tracking and deactivations of licenses on individual machines.
Our Customer License Portal allows Customers to organize and control license options easily, and we can help customize your Portal for easy management.
email:
Linux / Unix / WHM
For Linux machines, we use Secure FTP (sFTP) connections to upload our Blocklist to your CSF path every 15 minutes, in whichever format needed i.e.: csf.deny. We offer paid subscriptions through our website here.
Hackers have a multi-pronged approach to attacking American businesses and agencies. Most attacks are random, usually on your website or in the form of spam / phishing and attacks looking for vulnerabilities. When one is found, it is exploited.
Website & Email attacks include:
- Thousands of WP-Admin logins per hour
- SQL Injections
- Form and Comment spam
- Direct File Inclusions (malware/viruses)
- Denial-of-Service Attacks
- Email Bombing
- Phishing
Meanwhile, your public-facing servers are dealing with the same 'noise' attacks, while dealing with Windows-specific attacks such as Exchange Server exploits from Ransomware-as-a-Service (RaaS), Eavesdropping, Network Denial-of-Service Attacks, Spoofing, RTP Relays, Spim Attacks, Viruses & Worms, and so on, and so on.
These attacks result in slow networks, websites and email delivery; affecting productivity, increasing IT costs, and in worse cases, ransomware nightmares.
Ransomware attacks vary in their techniques, from simple phishing and malware infections to sophisticated proxy-shell flaw exploits. Hacker Blocker adds blockades to Ransomware at multiple stages:
- We research and block IP addresses and CIDRs used by Ransomware actors, including known RaaS (Ransomware as a Service) organizations such as BlackByte, which attacked the San Francisco 49ers on Superbowl Sunday, 2/13/2022
- We block IPs used by email servers that spread malware and phishing emails, substantially reducing the amount of spam and phishing emails
- We block IPs used by malware programs to communicate with their servers, stopping their ability to do their dirty work
- We recommend adding roles such as Anti-Ransomware FSRM to your servers, and educating staff to avoid phishing schemes
Exchange Servers using Hacker Blocker see immediate decreases in spam and phishing emails, increasing overall performance.
Windows - When your subscription expires, Hacker Blocker removes the firewall Rules it installed in Windows. Once you renew, it will download and apply the latest Rules once more.
Linux / LAMP - if your subscription expires, the IPs and CIDRs Hacker Blocker added are removed and no further updates are applied.
We do not offer a free trial, but we can offer free Detection, Reporting and Blocking apps for your website with every Linux order.
Yes! you can add user licenses for Windows Server, additional PC licenses or upgrade your Linux version to Unlimited website coverage.
We can customize any plan to your needs. Just contact sales for a free consultation.
Yes, you can cancel Hacker Blocker at any time, simply cancel your subscription online, uninstall the Windows version, or contact us for Linux cancellations.
The Hacker Blocker Blocklist has been compiled since 2016, and includes IP addresses & CIDRs of reported cyber-attacks from around the world. Our process is both reactive and proactive, as we collect attack reports from our customers as they happen, and from outside agencies before they happen to our customers.
- As attacks happen to our clients, we collect the IP address and research its origin
- Using our Whois tools, we find the CIDR of the IP. This can range from one to a million IPs on a single CIDR
- The CIDR is added to our own live firewalls, if it matches our criteria
- Our updated Blocklist is generated from our live firewall lists every 15 minutes
We only block the CIDR if it matches certain criteria:
- Small Network with multiple attack reports
- Large network from countries unfriendly to the USA (i.e.: Russia)
- Not a University or Medical Institution
Hacker Blocker installs a Service on your Windows machine that communicates with our secure servers and aquires our latest Blocklist. It then parses this list into Rules in your Windows Firewall. Hacker Blocker then updates your Firewall Rules every hour, as we constantly add and remove entries.